Mid of 2023 I was writing a little script to gather the information who invited a guest account and write that very information in an extension attribute from the user account. The plan was to run it on a schedules basis to monitor the audit log in Entra ID for these specific events and collect the informations for user lifecycle management.
Luckily Microsoft introduced their own solution for that some months ago with the sponsor attribute in Entra ID without any need for an Azure Runbook, fiddling around with “tid” or “oid” attributes and with even less permissions needed. Perfect, how?
You simply ask the Graph API for that very sponsor from a guest account. It’s really that simple and you even can see the inviting party in the Entra ID portal for e.g. folks from service desk without scripting skills. It hides behind the properties tab in a user profile under job Information.
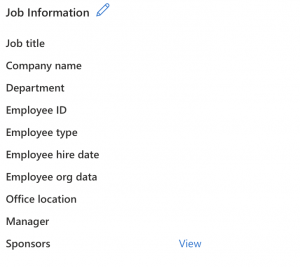
Although I noted in my tests that sometimes the list behind that view button misses the data. With the Graph API I was apart from that always lucky finding the needed data. So – how do we do that?
Connect-MgGraph -Scopes "User.Read.All" -ContextScope Process
# Search for the guest user
# You could loop that of course through alle guests in your tenant
$Guest = Invoke-MgGraphRequest -Method GET "https://graph.microsoft.com/v1.0/users/?`$filter=mail eq 'user@guestdomain.tld'
# Build the uri
$URI = "https://graph.microsoft.com/v1.0/users/$($Guest.Value.Id)/sponsors/"
# Get Sponsor from guest id
Invoke-MgGraphRequest -Method GET $URI | select value -ExpandProperty Value
Name Value
---- -----
preferredLanguage de
@odata.type #microsoft.graph.user
officeLocation
jobTitle
surname Kaiwe
mobilePhone
mail user@guestdomain.tld
givenName Tim
businessPhones
id 841e8808-0000-40b0-a54b-57129c4188fe
userPrincipalName Tim.Kaiwe@cloudkreise.onmicrosoft.com
displayName Tim KaiweYou could now example given automatically trigger an access review to audit the access permissions or need for that guest user in your tenant to the sponsor and remove it if not needed anymore. Hope that little titbit was as interesting for you as for me.
